Abstract
The paper focuses on the application of Geographical Information Systems (GIS) in the Kingdom of Saudi Arabia to combat terrorist activities. Even though the Internet became a tool of mass destruction, upgraded information systems can help in understanding the landscape where the presence of terrorists is suspected. Thus, GIS can help in crime mapping and countering terrorism. Different tools and methods related to GIS technology are discussed here and their applications in ensuring effective security measures are focused upon. GIS provides the technology that enables geographical data collection from LIDAR, aerial photography and satellite imagery, data that is captured, stored, analysed and displayed in maps. The maps can reflect hot-spot gas field and oil field where terrorist activities are carried out. This also makes geography a key subject in understanding such activities. Apart from terrorism, the public health sector also has a huge application for GIS. Such technological method requires effective mapping and when combined with geospatial technologies, terrorism can be countered with appropriate action. The age of big data, digital mapping and other remote sensing technologies are discussed in the paper.
Keywords: Geographic Information System, GIS, Counter terrorism, Geographical data collection, KSA, Egypt, Lidar
Cite this paper: Awatef Alsharif Shejaa Ali Alharith, Yasser Abdelazim Abdelmawgoud Samak, Fighting Terrorism More Effectively with the Aid of GIS: Kingdom of Saudi Arabia Case Study, American Journal of Geographic Information System, Vol. 7 No. 1, 2018, pp. 15-31. doi: 10.5923/j.ajgis.20180701.02.
Article Outline
1. Introduction
This paper explores the role that Geographic Information Systems (GIS) can play in combatting terrorism in the modern world, both for activities designed to prevent terrorist events from occurring in the first place and activities designed to deal with the aftermath of a terrorist event.
2. Terrorism and the Internet
In this century, the Internet has become a favored weapon for mass destruction as well as a convenient means of communication for terrorists. Research by Furnell and Warren (1999) has found that various terrorist groups and organizations make regular use of the Internet and its information to plan and support their different acts of terrorism and then to carry out their attacks on the global Internet itself as well as on people. They use it too to communicate with people all over the world. Its advantages as a weapon of terrorism are manifold, as it can be accessed by a person anywhere, irrespective of their country, city or locality, and these days, even by a cellular phone. The use of the Internet to carry out an attack produces a result within a few seconds, and, critically, the attack cannot be traced back to the guilty parties as they can hide behind anonymous identities and confidential applications and techniques.
Thus, it can be used to cause bodily harm and death to people, to damage buildings, to cause plane and train crashes, and explosions in highly populated areas such as market places and shopping malls. It can also be used to execute large scale attacks on IT infrastructure with the use of bot-nets, viruses and Trojan elements that block the system and then institute terrorist control. It can be used to hack into protected information and data by exploiting the shortcomings of installed security systems. Government computer systems have been hacked many times by terrorists, for instance, to gain access to highly classified information on key matters. It can be used in hybrid attacks which combine a bomb attack and the simultaneous blocking of the communication systems used by the police force and medical services to cause massive loss of lives and damage to property. Attacks aimed at physical damage are based on manipulation of Supervisory Control and Data Acquisition (SCADA) systems (connected to the Internet for increased connectivity) and are the most damaging of all attacks as they contribute directly to the injury and deaths of the general population and to damage and destruction of infrastructure (Storm, 2014).
2.1. The Role of GIS in Terrorism, Public Health and the Internet
The deployment of Geographic Information System (GIS) through the Internet is creating new benchmarks as well as posing new problems for effective use of the web-based geospatial applications. Spatial scale, data file size and other conditions for extensive use of GIS comprise the challenges. For the public health domain, geospatial databases built for the Web are required to maintain confidentiality in order to prevent disclosure of an individual’s identity. GIS combined with Web technologies help in solving problems, analyzing geospatial data, providing solutions to problems and presenting the information in visually friendly format such that public health decision makers can see and understand it with ease (Croner, 2004). GIS technology is also used in mental health research areas such as epidemiology, service utilization and the impact of neighborhood on mental status analysis. GIS-based spatial mapping can be used for rendering a better analysis of patterns of illness, its causes, impact and needs for service. Such information can help in assessing the nature of an intervention and help in formulating health policies based on evidence (Walsan, Pai and Dawes, 2016). GIS tools especially the 3D applications of hot spot identification or mapping the trends in a geographical region are used for preventing crimes and terrorism. Despite use of the Internet, terrorists are sensitive about spaces and places, especially for their training, planning and other operations. Therefore, geo-spatial tools will find great applications in tracking terrorist activities (Medina, Siebeneck and Hepner, 2011).
Geography is a key means of addressing the problem of terrorism, and GIS can even be used to track terrorist activities. As globally important events like climate change and political violence occur now, people agree and appreciate that geography is an important discipline which can connect local to global events (Haney, 2017). For instance, protection agents can use 3D models for general analysis of an area. Digital photos of a landscape can display a 3D view which may be rotated based on the angles shown in detail in the landscape. For protection of a place from harmful activities such 3D views can obviously help. A viewshed, for instance, can also be created with GIS for a line such as a path along which a target could walk or drive. If view sheds are created using Digital Surface Models (DSMs), visualization and area estimation of a region where a target could be vulnerable can be built. Using 3D digitally spatial information analysts can recreate areas with real life photos and imagery overlying the Sketch Up buildings (i.e. buildings produced by Sketch UP software). This could minimize the cost of multiple trips to an area by protection agents (VanHorn and Mosurinjohn, 2010).
2.2. Saudi Arabia’s Position
The Kingdom of Saudi Arabia (KSA) occupies around four out of five parts of the Arabian Peninsula which is a mass of land bounded by the Red Sea on the west, Indian Ocean on the south and Arabian Gulf on the east. The country has a land area of 2,250,000 square kilometers. Jordan, Iraq and Kuwait lie to its north, the Gulf, Qatar and the United Arab Emirates on its east, and the Sultanate of Oman and Yemen lie to the south. Since 1966 Saudi Arabia and Kuwait, located adjacently were separated by some neutral territories referred as the Neutral Zone. The Kingdom and Iraq were separated by another Neutral Zone. The Kingdom lies in a strategically important position with a long boundary lying along the Red Sea and the Arabian Gulf. It is situated between Africa and the main lands of Asia while the Suez Canal is near its north-west border (Profile of Saudi Arabia, 2017).
Saudi Arabia is one of the few countries where the fight against terrorism and extremism has yielded real successes. This success cannot be explained only by the effectiveness of its security measures, but also by its non-aggressive approach in tackling radical ideologies (Ansary, 2017). The Saudi government realized that existing security measures were insufficient and recognized the essential role of radical ideology in motivating terrorists and justifying terror. The Saudi government re-crafted its strategy to take on the radical ideologies that foster violent extremism. As a leader in the Muslim world, Saudi Arabia is committed to demonstrating serious determination and responsible leadership to eliminate the mentality of extremism and violence that perverts the Islamic religion.
Since the 1983 oil discovery, Saudi Arabia has become in the world’s largest oil exporter, which has allowed it to transform into the twentieth largest economy in the world. With measured oil reserves passed only by Venezuela’s, Saudi Arabia has had enormous human development, which has also converted Arabia into the focus for terrorist attack. It has also put the country into a critical position, where the management of geographical information is of vital importance for accurate and detailed knowledge about its territory, its various resources, and for the execution of preventive and contingency plans when facing terrorism (Difiglio, 2014).
Knowing the territory is fundamental for the development of strategic activities specifically for the army, whether on the ground, on the sea or in the air. Displacements and operations in all types of terrain (plains, mountains, deserts, marshes and others), both on foot and in all types of vehicles, obligate security officials to have detailed knowledge of all these elements, especially the surface ones (both natural and artificial), as well as all other smaller geographical features: flora, fauna, geological base, natural resources, etc (Satyanarayana and Yogendram, 2002). Additionally, every aspect of the climate and the meteorological conditions must be considered too, since it governs the use of the terrain in its three dimensions (Storm, 2014).
Anti-terrorism efforts will be better served if we input all this information into a Geographic Information System in order to integrate of all these elements into a single usable coherent whole.
3. Geographic Information Systems
Terrorism can be most effectively combatted by using the same Internet that terrorists rely on for their activities, but in the case of counter-terrorism though, the power and versatility of the Internet is best harnessed by Geographic Information Systems (GIS), a tool for information analysis.
GIS comprises hardware, software and procedural systems, designed to support the capture, administration, manipulation, analysis, modelling and graphing of referenced geographic data and objects, especially to solve questions involving complex planning and management – such as security issues, or issues relating to health care or to the spread of infectious diseases or even to responses to natural disasters. GIS allows comprehensive analysis of the territory including the most diverse areas. It is an extremely versatile tool, with a wide field of application to any activity involving a spatial component. Consequently, in the recent years GIS technology has been used in the military field, in scientific research, for resource and asset management, as well as in countless other fields such as archaeology, environmental impact assessment, urban planning, cartography, sociology, historical geography, marketing and logistics, to name just a few (Dempsey, 2011).
GIS is now indispensable for any decision-making by government, in which spatial information has a special relevance and for which simple maps are insufficient. The success (or failure) of the planning of preventive measures against terrorism and the consolidation of security in conflict zones also depend in many cases on such spatially related decision-making by government. To do this requires planning. The first stage, monitoring, involves data gathering. The second stage, preparedness, concerns risk assessment which involves target identification and location analysis. The third stage, response, is about data sharing in GIS which involves Big Data technology implementation. The fourth stage, mitigation, includes prediction of the location, frequency and severity of terrorist attacks, and also activities designed to counter terrorist activities by planning and execution (Chandrakar and Thomas, 2010).
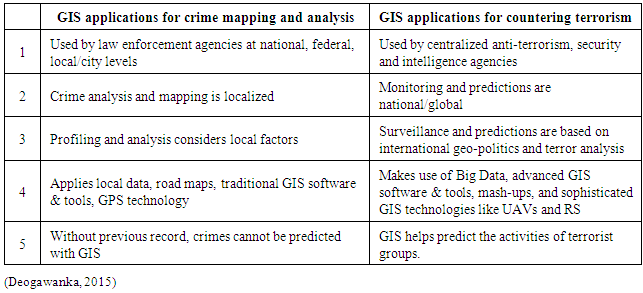
3.1. Crime Mapping and Counter-Terrorism
There are differences between the use of GIS technology in crime mapping and countering terrorism, and these are outlined in Table 1.
|
3.2. GIS and Related Geospatial Technologies
GIS and related geospatial technologies, like Global Positioning Systems (GPS) and satellite Remote Sensing, along with digital aerial photography image processing can help counter terrorism acts.
GIS together with these other technologies can help in intelligence analysis. Satellite imagery and Light Detection and Ranging (LIDAR) data, for example, can help in the understanding of an area of terrorist activities and the development of strategies with a high level of accuracy (Magnotta, 2015). Unmanned aerial vehicles (UAVs) can help identify positions, take photographs and access areas which are otherwise inaccessible.
GIS can be used to simulate scenarios involving terrorist attacks and targets who are difficult to track.
GIS can help coordination of the immediate response to a real attack by providing knowledge about the proximity of the attack sites (Can and Leipnik, 2010).
GIS and GPS, along with airborne technologies like aerial videography and infrared detection LIDAR, can help to assess the short and intermediate term effects of an attack and help to establish the boundaries of evacuation zones, locate evidence and rescue victims (Can and Leipnik, 2010).
GIS produced maps are a critical component for monitoring terrorist movements, communicating with ground operations and combating terrorism.
3.3. Unmanned Aerial Vehicles (i.e. Drones)
Drones are unmanned airplanes (sometimes called Unmanned Aerial Vehicles – UAVs) powered by an engine and capable of autonomously maintaining controlled and sustained flight. They come in a wide variety of shapes, sizes, configurations and characteristics, and can either be controlled from a remote location, or can fly autonomously on pre-programmed flight plans via dynamic automation (Gertler, 2012).
The main drive to improve the technology of UAVs comes from the military. In warfare their use may have significant advantages, such as the possibility of avoiding the death of a pilot, for instance (Bruntstetter, 2012). Free of the limitation of having to carry a human, drones are very maneuverable. At present the most extensive applications of these advantages are in warfare related activity. Drones are specifically designed for combat, and also for intelligence tasks – revealing the enemy’s hiding places, for instance. Such drones can be extremely small and difficult to notice (Bruntstetter, 2012).
3.3.1. Advantages and Disadvantages of Drone Usage
One of the main advantages of drone usage comes from the reduced cost for obtaining aerial photographs. By avoiding the expenses of airport taxes, fuel, pilots, and so on, drones become cheap enough to use (SRI International, 2013).
According to the capabilities of a particular device, a drone might be very time efficient as it might be able to fly for several days at a time, or be equipped to fly at night, which, for some technical or rescue work, could be exactly what is required.
The use of drones reduces personal risk too, as they are able to enter areas contaminated by fumes, gases, toxic spills, etc., thus avoiding possible health risks to humans. The dimensions and maneuverability of a drone allows it to access areas in which a manned aircraft could not be maneuvered (SRI International, 2013). Drones are often preferred for missions that are too “boring, dirty or dangerous” for manned aircraft (Phil for Humanity, 2017). UAVs are also used in a small but growing number of dangerous civilian applications, such as fire-fighting or civil security, and also in pipeline surveillance.
Their ability to maintain stabilized stationary flight at a specific point is an advantage as it allows for high quality photographs and aerial videos. Currently, military UAVs perform both reconnaissance and attack missions.
While many successful drone attacks have been reported, they can cause collateral damage and/or identify erroneous targets (Vogel, 2011), which is a particular disadvantage.
4. Data Gathering by Remote Sensing
Several Remote Sensing (RS) methods are available for use in data gathering for GIS, the most prominent one being Light Detection and Ranging (LIDAR).
4.1. Light Detection and Ranging
Light Detection and Ranging (LIDAR) is a surveying method that measures the distance from its laser emitter to an object/surface using a pulsed laser beam. The distance to the object is determined by measuring the time delay between the pulse emission and detection of the reflected signal. This technology has applications in geology, seismology and physics of the atmosphere, thus making its information an indispensable complement of any GIS development. LIDAR produces higher quality results than conventional techniques do. The challenges involve an increasing volume of data and the increased efficiency required for its software processors (Wehr, 1999).
After putting the data through an Airborne Laser Scanner (ALS), LIDAR produces a cloud of points on the terrain. Two movements are combined for the ALS, a longitudinal one given by the trajectory of the plane, and a transverse one by a movable mirror that deflects the beam of laser light emitted by the scanner.
To ascertain the coordinates of a cloud point, the position of the sensor and the angle of the mirror need to be known at all times. For this purpose, the ALS system is based on a differential GPS system and an inertial navigation sensor (INS). Using both sets of data, the desired coordinates are produced at the rate of tens of thousands of points per second (Marqis, 1993) to produce a cloud profile. These can be used to produce images such as the sample shown in Figure 1.
 Figure 1. Example of an image produced from LIDAR data after LIDAR surveying from a plane
Figure 1. Example of an image produced from LIDAR data after LIDAR surveying from a plane
The use of LIDAR data enables the production of longitudinal profiles of any desired segment with high precision. The application of these LIDAR techniques reduces the high costs generated previously by field brigades, and homogenizes the results obtained remarkably, since it is not dependent on the quality of measurements made in the field, and is able to be carried out even in difficult-to-access areas. Digital terrain models (DTM) and digital surface models (DSM), based on cloud profiles, are extracted from the LIDAR data. A DSM model, i.e. one that includes surface objects on it, is shown in Figure 2, but either format can be easily produced by GIS systems (Wehr, 1999).
 Figure 2. Example of a Digital Surface Model (DSM), i.e. with objects on the terrain’s surface
Figure 2. Example of a Digital Surface Model (DSM), i.e. with objects on the terrain’s surface
Such data collection is very useful because LIDAR’s multi-return LASER sensor, allows the collection of data below the vegetation, as can be seen in Figure 3. It thus permits detection of installations that are not perceptible to any type of aerial photography, therefore allowing security forces to carry out preventive operations on the area (Carter et al, 2012).

The cloud profile view of terrain points, in which all non-terrain elements were removed leaving only clear terrain data, as can be seen in Figure 4. Security forces, for example, can use this to plan an ideal action in the area.

The main advantages of the use of LIDAR for the sampling and capture of territorial information include the following.
All data is recorded digitally, which makes it possible to process it automatically in a few hours, using various computer packages available on the market, to produce useful results of high accuracy.
The laser is an active sensor, which is remarkably independent of the atmospheric conditions and solar light.
It is possible to define a large number of acquisition parameters.
It is based on an aerial sampling in which information is collected quickly and accurately and without the need for terrestrial support, which is very useful for sampling difficult to access areas.
The products derived from processing the cloud points are very useful, and they complement the GIS, providing information of high precision that is not obtained by any other type of sensor (Shekhar and Xiong, 2007).
4.1.1. New Application for Remote Sensing
It is well-known that RS such as LIDAR is conventionally applied to the exploration and monitoring of land and geographical aspects. However, the use of RS technology to fight terrorism comprises an innovative use of this technology. Pakistan, for instance, has been doing this, and their geospatial community is constantly at work on it. Their security agencies use geospatial data to understand the patterns of terrorist attacks, and their rescue workers use it to help save lives by locating where help is required. But the data for these uses needs to be updated regularly – as the utility of the data decreases, if it is outdated. Updating the data is difficult though, due to the law and order situation in Pakistan. The datasets are usually collected by continuous ground surveys which take over five years for one round. To resolve that situation, Pakistan has had to resort to a mix of traditional military warfare tactics with optimum use of geospatial knowledge, such as RS, which may lead to asymmetric warfare. Asmat (2010) has analyzed the supporting role of RS in helping antiterrorism and rescue efforts.
The King Abdul Aziz City for Science and Technology (KACST) in the Kingdom of Saudi Arabia (KSA) organized a three-day event in 2017 (Wamda, 2017), which was co-sponsored by various well-known companies in the country, and more than 30 companies took part. Previously, the city had mainly used RS technology for developmental purposes, but the KSA is on its way to becoming a knowledge based economy, and plans are being formed to increase its satellite capabilities.
This will in turn meet the needs of the country, and even allow for GIS application in fighting terrorism, which has essentially four components: “when, where, how, who”. During a terror attack, geospatial tools and techniques would help in securing citizens and property from terrorist operations. Terrorist activities are prominent in the media, and analytics have been designed to help counter them by forecasting attacks and financial sources. A lawyer has suggested data mining is actually a means of fighting terrorism (Dycus, 2016), when it helps extract valuable information from various sources. The patterns so obtained can help predict the activities of terrorists, and, in turn, facilitate methods of controlling them.
4.2. Digital Orthophoto
The data obtained from remote sensors, such as aerial photographs and satellite images, is very useful when it shows directly and clearly the features of the terrestrial surface. Besides being the basic source for cartographic information, it can be used directly to feed GIS and other diverse applications such as for the military.
The aerial images obtained by aerial sensors do not have the geometrically common scale necessary for cartographic works. Through photogrammetric processes, though, these images are corrected to meet the required geometric set of specifications, and together with a geo-reference, they comprise what are known as digital orthophotos (Zhou et al, 2004).
4.3. Aerial Photography
Aerial photography provides an exact representation of the land at the time it was taken, contains useful information for the various areas related to the Earth sciences, and is a basic element for the generation of models and products for the knowledge about the territory concerned. It is one of the fundamental inputs into topographic, cadastral and risk mapping, as well as for land management and other topics related to the provision of basic information for analysis of the geographic environment. In military spheres these stereoscopic images allow a clear and precise panorama with a three-dimensional perspective of difficult to access areas, or simply allow remote analysis (Audu and Sadka, 2014).
4.4. Satellite Data
Satellites are devices designed to observe the Earth from an orbit of one of two types. Low earth orbits (LEOs) are designed for the exhaustive exploration of the Earth’s surface, such as for fire detection, biomass determination and study of the ozone layer among other functions.
Geostationary satellites (GEOs), on the other hand, specialize in meteorological studies (Audu and Sadka, 2014) The main satellites used as Special Interest Group satellites (SIGs) are Radar Sat, European Remote Sensing Satellites 1 and 2 (ERS-1 and ERS-2), Shuttle Radar Topography Mission (SRTM), Pleiades, Worldview-2, Geo-eye, Quick Bir and SPOT. Surveillance satellites provide multispectral images (MSI) of the surface and detect surface changes. The images, whether military or civilian, depend on a compromise between the resolution provided and the surface covered: the higher the resolution, the smaller the area of the displayed surface. Meteorological satellites are designed to provide accurate and timely meteorological data including specialized meteorology, oceanography, and solar geophysical data. Navigation satellites provide accurate positioning in two or three dimensions with worldwide, speed and time data. The signals are transmitted to the ground for naval and air forces equipped with navigation receivers (Helms, 2011).
5. Using GIS to Counter Terrorism
GIS can be implemented for the prevention and combat of terrorism, but it has to be particularized by the user for a determined purpose by means of a set of procedures on non-graphical (i.e. descriptive) databases relating to the real world. Within the GIS, large-scale graphic and alphanumeric processing tools are used. These tools are equipped with procedures and applications for capturing, storing, analyzing and displaying geo-referenced information. The greatest utility of a Geographic Information System is that it has a closely related capacity for constructing models (i.e. representations) of the real world from its digital databases; this is achieved by applying a series of specific procedures that generate even more information for analysis. The construction of models (“models of simulation” as they are called), by means of hot spots, becomes a valuable tool for analyzing phenomena that relate to tendencies, and by this means the different influential factors can be established(Marina, 2012). Figure 5, for example, shows the main places, with the help of some hot-spots, where terrorist attacks are concentrated.

5.1. Kernal Density
A raster is generated for kernel density by calculating the density of the point entities around each output raster cell, and is used for the density of an area rather than a single point; it is higher at the point location and decreases as the distance from the point increases and reaches zero at the determined search radius distance (1km) from the point of origin. This is illustrated in Figure 6 (ArcGIS, 2017).
Kernal density is used for measuring the intensity of certain characteristics around those features for their point and line characteristics. For point features, Kernel density measures point features around every output raster cell, which helps in finding density of houses, roads, utility lines and so on which influence habitats. The population field is usually used to put more weigh on some features than others, and can allow one point to represent many observations. For instance, one address might represent many units (ArcGIS, 2017).

5.2. GIS and Its Use of Data
GIS provides the functions and tools needed to store, analyze, and deploy geographic information. The main components of the programs are as follows.
1. Tools for the entry and manipulation of the geographic information
2. A database management system (DBMS)
3. Tools for geographic searches, analysis and visualization
4. A graphical user interface (GUI) for easy access to the tools (Meurant, 2012).
Probably the most important part of GIS is the data. Geographical and tabular data can be acquired by whoever implements the information system, as well as by third parties who already have it available. The GIS integrates spatial data with other data resources and can even use the most common database handlers to handle geographic information (Yeung and Lo, 2007).
To be able to take into account information about the whole territory and to classify it strategically (as in Figure 7), only the primary routes of communication that are indispensable before a terrorist attack can be identified (Medina, Siebeneck and Hepner, 2011).
 |
Figure 7. Strategic map of the entire territory of the KSA |
With such a strategic map, it then becomes possible to analyze diverse situations like the following.
- Ideal routes for police and militia movement to the point of an attack
Evacuation routes before an attack
Measurement of distances and travel times
Location of strategic communication points necessary to reinforce security and so on.
The management of the GIS requires the necessary personnel to operate, develop and administer the system. Models applicable to real world problems have to be constructed before it is possible to mitigate terrorist attacks, or, in case of an event, to make it possible to act effectively and reliably for the benefit of the population and national security (Medina, Siebeneck and Hepner, 2011).
When initiating the study to design a GIS that allows for prediction of the different types of terrorist attacks, it must be remembered at all times that terrorists are going to use objects that exist in the real world, that those objects have differentiating characteristics and those objects retain certain spatial relations that must be conserved. As a result, the GIS has to be developed based on models of the objects and their relationships that are found in the real world (Medina, Siebeneck and Hepner, 2011).
5.3. Storage of Information in GIS
Correct storage of the geographic and descriptive information occurs in four large sets of GIS databases, which allow accurate analysis to be carried out. These databases are: Image Databases, Supplementary Image Databases, Map Databases and Descriptive Information Databases.
5.3.1. Image Databases
Image Database images, such as those in Figure 8, represent the terrain in various temporalities and allow perception of any territorial evolution, and thus analysis of the before and after effects of any type of terrorist attack. The amount of detail and the precision of the analysis depend on an image’s resolution, obtained as it is from drone, plane or satellite (Franco Plata et al, 2012).
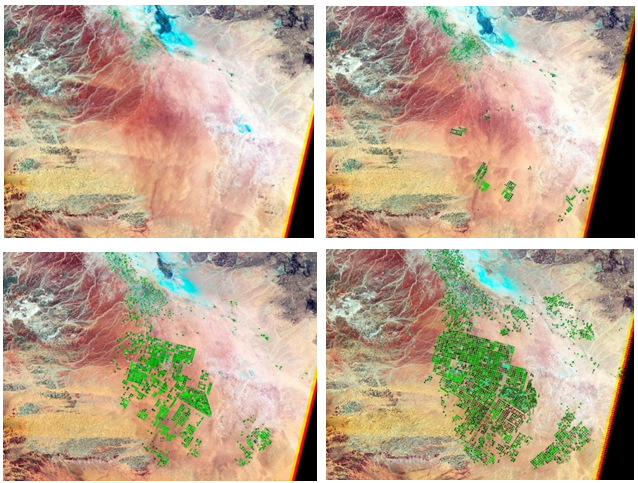 |
Figure 8. Images from an Image Database showing an increasing degree of resolution |
5.3.2. Supplementary Image Databases
Graphic symbols and alphanumeric characters from the Supplementary Image Database geo-reference the same coordinate system of the actual images they relate to (Boerma, Mol and Jolles, 2016). Figure 9, for example, shows a version of the strategic map of just a section of the territory previously shown in Figure 7’s strategic map of the KSA.
 |
Figure 9. Example strategic map of the KSA from the Supplementary Image Database employing graphic symbols |
5.3.3. Map Databases
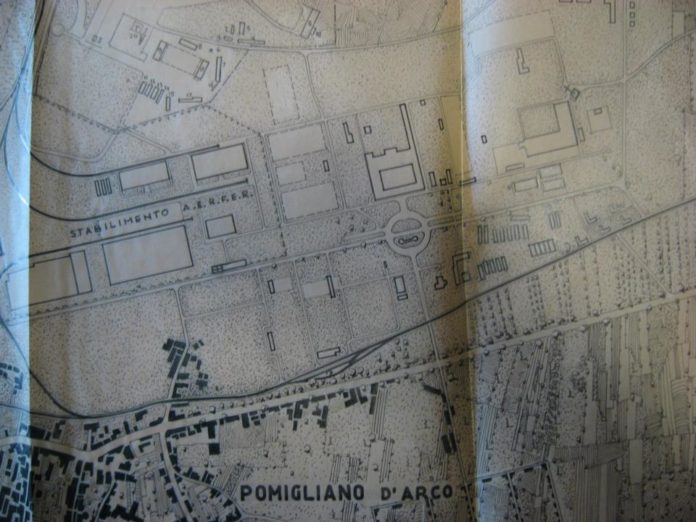
Maps (such as the one in Figure 10) from the Map Database represent different kinds of information for a specific area, corresponding to the different coverage and categories appropriate for mapping (Paliouras, Spyropoulos, and Tsatsaronis, 2011).
 |
Figure 10. Example map of the City of Assiut from the Map Database |
5.3.4. Descriptive Information Databases
Descriptive data (such as what is shown in Figure 11) from the Descriptive Information Database is stored in the most commonly used forms, so it can be used by other systems. Information manipulation includes extraction and editing operations (Bourgeois, n.d.).
 |
Figure 11. Example of descriptive data from the Descriptive Information Database, with information specific to different regions being extracted |
5.4. Extraction/Retrieval of Information in GIS
Methods of information extraction or retrieval from GIS are very varied and can be very complex. The basic method is to specify a spatial domain defined by a point, line or desired area. For example: it is possible to select through GIS the oil zones in a separate plan, or oils zones that are part of the country’s financial wealth and therefore possible targets of attacks designed to destabilize the economy or for other reasons.
The main steps for extraction or retrieval of information from GIS are the following.
1. Extraction by geometric specification
2. Extraction of graphic entities of the points of interest by means of spatial domain and geographical condition, e.g., oil energy reserves and gas in a given radius (Rock, 2011)
3. Extraction by geometric condition
4. Extraction of certain space entities that satisfy a given descriptive condition, e.g., all oil fields in the same geographical area
5. Extraction by descriptive specification, such as gas or oil
6. Extraction by descriptive or logical condition, e.g., pipelines longer than 100km
7. Extraction of spatial entities that fulfill the descriptive condition and any logical expression related to some of its associated spatial attributes, e.g., all pipelines from the same region and longer than 100km
8. Extraction of the information in the layer attribute tables
5.5. Editing Information in GIS
The capacity to edit the information in the GIS allows for its modification and updating. The editing functions are particular to each GIS program, but should include: mechanisms for editing graphic entities (color, position, scale, and drawing of new graphic entities, among others); and mechanisms for editing descriptive data (modifying attributes, changing file structure, updating data, or generating new data, among others). Editing functions allow the performance of the analytical operations necessary to produce new information based on the existing information to solve a specific problem.
The handling of GIS information allows us to obtain accurate and useful results to determine areas that, for various reasons, are sites of potential conflict and thus attack (Mihira, 2017). Figures 12 and 13, for example, show results of the analysis and manipulation of information regarding a hot-spot Oil Field and hot-spot Gas Field respectively.
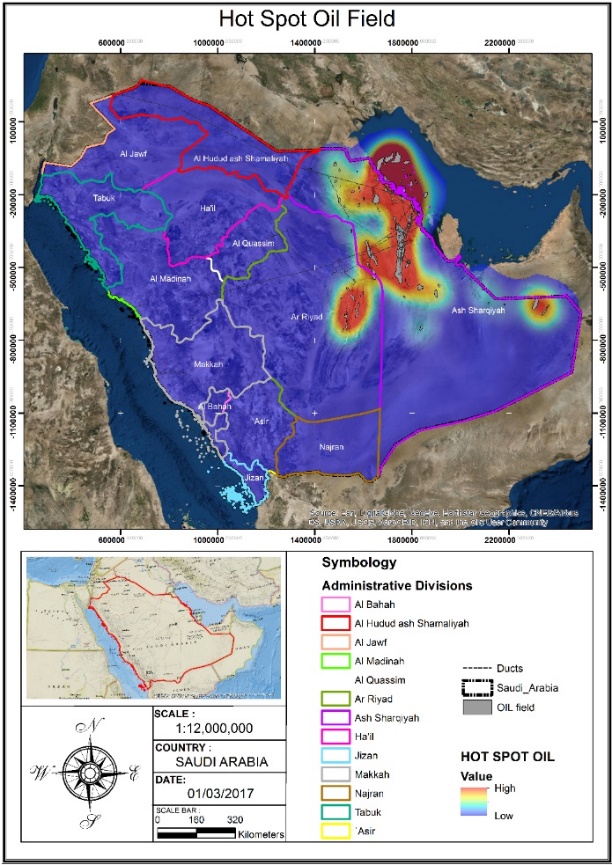 |
Figure 12. Model of a hot-spot Oil Field based on information extracted from GIS |

5.6. Analysis and Modelling of Information
Analysis and modeling is obviously of prime importance. Its operations can be classified by:
Capacity of the characteristics of a map or cartographic presentation to generalize in order to make the final model less complex
Cartographic generalization
Spatial analysis
Analysis of the obtained information requires functions that perform calculations for the graphic entities focused on obtaining results to prevent a terrorist attack, or to act in that case. Such analysis and modeling for this derives from simple operations like finding simpler ones like longitude, perimeter, areas and volumes, to more complex ones like the analysis of driving networks, and the insertion of polygons and analysis of digital models from the derivate field of LIDAR technology (Zhou et al, 2004).
There are various different types of analysis that a GIS can perform.
1. Contiguity analysis is used to find certain areas in a determined region
2. Coincidence analysis is used to analyze the overlap of points, lines, polygons and areas
3. Connection analysis is used to analyze graphic entities that represent networks like:
a. Routing is about how the driven element moves through the network
b. Range of action is about how the range of an element’s movement inside the network
c. Pairing addresses is about connecting any addresses to the graphic entities
d. Digital analysis of the field with LIDAR technology is about analysis of the surface information to make a model for continuous geographic phenomenon. Such analysis is performed with high quality digital models of the land and the cloud that contains the points and exact X, Y, Z coordinates of the entire area, which is the basic data for analysis and positioning of the surfaces.
e. Operations over the maps is about logical and mathematical calculations for the analysis and modeling of the geographical attributes. These operations are supported according to the data format used (raster or vectors).
f. Geometry of the coordinates is about geometrical operations for the handling of terrestrial coordinates using logic and mathematical operations. Some of these operations include terrestrial projections of the maps, geometrical transformations (rotation, translation, and scale changes), coordinate precision and correction of errors (Mihira, 2015).
5.7. Digital Elevation Model
Digital elevation models are a kind of raster GIS component which views the world as a proportionate arrangement of places. In such a model every cell has a value denoting its elevation. When locations are arranged in proportion, interesting inferences can be drawn. Adding hill shading is an important component of such maps so the association of terrain and its surrounding can be mapped. Rasters represent the world in a regular organization of pixels, which leads to systematic analysis of the associations between places and their assets (PBC GIS, 2017). An example of a digital elevation model can be seen in Figure 14, which clearly shows its useful nature.
 |
Figure 14. Digital Elevation Model showing the relief variation on the border between the KSA with Yemen |
5.8. Exit and Representation of Information from a GIS
The information output of a GIS can be textual or graphic, and both can be presented in either digital or printed form. Digital representation is used when such information is systematized in a Geospatial intelligence center that is the Command center of the operations and generates analyses. Textual information usually consists of a set of tables representing either the information stored in the database, or comprises the results of some type of analysis performed on the database. Analog graphic information consists of maps, graphs or diagrams. All of this data feeds the system to enable highly accurate analysis that can be used to formulate scenarios against possible future terrorist attacks and to enable security systems to take preventive measures. The system must provide the capacity to complement the graphic information with suitable symbols before its final presentation, and also to add geometric elements that produce a quality visualization that users can easily understand (Bernsen and Dybkjaer, 2009). Such a high-quality visualization with added symbolic and geometric elements can be seen in Figure 15.
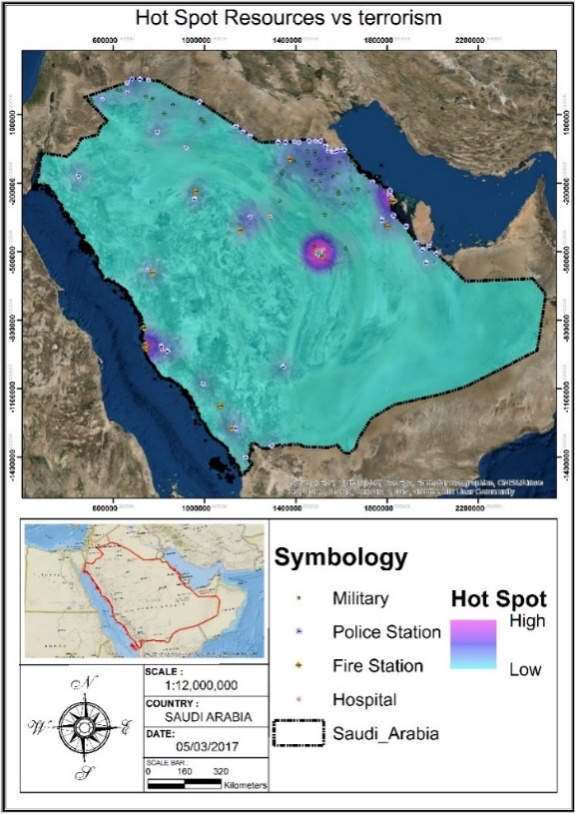 |
Figure 15. Example of a high-quality graphic representation of hot-spot Resources vs Terrorism with added symbolic and geometric elements |
5.9. Utility of the Information Obtained with a GIS
A GIS contains a set of specialized procedures capable of storing and manipulating geographically referenced data, i.e., objects that have a defined location on the earth’s surface and are included in a conventional coordinate system (De By, 2001). With the combination of diverse information concerning the terrestrial surface, that contains a physical dimension as well as a spatial localization, the GIS will allow as much analysis as is necessary in order to combat terrorism.
5.10. Example of GIS Use in Operation Desert Storm
Operation Desert Storm 1990-1991, was known as the first space war, and it can be said that it was the first virtual war of the 20
st
- century as well.
The US Army’s Geographical Information Systems was used during it in conjunction with data from six satellites from three separate systems. The satellites broadcast continuously, providing infrared and microwave visual data, and constantly provided this information to Operation Desert Storm’s base of command for the operations (NOAA, 2017).
Land and air commands relied on weather satellite support for planning purposes, ammunition selection, reorientation of combat flights and reconnaissance missions, ground movement planning and equipment optimization for night vision and focusing systems for watching during the night. With the advent of laser-guided weapons, the need for clear weather conditions placed greater emphasis on accurate weather reports. Weather satellites provided information that was able to alert troops to sandstorms, to predict the possible spread of chemical agents and to monitor the burning of oil wells. One of the satellites of the Meteorological Defense Satellite Program (DMSP) was launched in December 1990 to increase coverage and had the additional capacity of detecting areas of moisture and stagnant water through microwave imagery. The Coalition made use of SPOT’s stereo imaging capabilities by producing videos of stereoscopic images of the objectives and flight paths for briefing sessions prior to pilots’ flights (NSIDC, 2017). Figure 16 contains a sample of a GIS sent by (USA) in Operation Desert Storm.
 |
Figure 16. Sample GIS sent by USA in Operation Desert |
The advantages provided by the satellites and the data obtained through the US Army’s GIS was highly favorable and decisive in the operations and decisions that were made during the Desert Storm conflict.
6. Conclusions
The Internet can be used as a means of communication by terrorist organizations to present their views, issue threats to the general public and government organizations, find new supporters, train followers and communicate with their followers and confidantes. Considering the concealed nature of their work, the global Internet provides them with an opportunity to interact with the world directly, which is also less time-consuming and less risky than previous communication methods.
The graphic materials and satellite maps available on the Internet also provide them with an effective tool for planning terrorist attacks, and devising escape routes with greater precision. It can be stated that, nowadays, using techniques similar to the ones used by normal users of the Internet’s services, terrorist organizations are capable of attacking all sites that are interlinked with the global Internet. The most important sites which attract cyber terrorism activities are the telecom industry, the energy industry and the finance sector.
However, these same Internet-based tools can also be used by Security forces to monitor terrorist organizations, and significantly, use remote sensing in fighting terrorism. To do this effectively, a system that allows for the collection, analysis and display of all the relevant geographic data supplied by the various RS technologies, in other words, a GIS, is a must. Using a GIS also allows for access to updated geo-information of the area concerned, so any information displayed is current and therefore critical.
RS technology and GIS are not only useful for the exploration of simulated warfare scenarios involving potential attacks at obviously critical sites, such as the telecom industry, the energy industry and the finance sector in particular, but are also an essential aspect of countering terrorism attacks at other less obvious sites.
GIS can also be used to display all up-to-date geo-information about terrorist suspects for monitoring and analysis to learn as much as possible about them, in order to help curb the spread of their deadly ideology.
With all this geo-information available, the only way to handle it effectively is by the use of GIS.
ACKNOWLEDGMENTS
This project was funded by the Deanship of Scientific Research (DSR) at King Abdulaziz University, Jeddah grant no: G-228-246-38. The authors, therefore, acknowledge with thanks DSR for technical and financial support.
References
Awatef Alsharif Shejaa Ali Alharith1, Yasser Abdelazim Abdelmawgoud Samak2
1King Abdulaziz University, Department of Geography and GIS, Faculty of Arts and Humanities, Female Student Department Al Sulaymaniyah Branch, Jeddah, Saudi Arabia
2Faculty of Arts, Department of Geography and GIS, Assiut University, Old University Building, Assiut, Egypt
Correspondence to: Yasser Abdelazim Abdelmawgoud Samak, Faculty of Arts, Department of Geography and GIS, Assiut University, Old University Building, Assiut, Egypt.
| Email: |  |
Copyright © 2018 Scientific & Academic Publishing. All Rights Reserved.
This work is licensed under the Creative Commons Attribution International License (CC BY).
http://creativecommons.org/licenses/by/4.0/
Pubblicazione gratuita di libera circolazione. Gli Autori non sono soggetti a compensi per le loro opere. Se per errore qualche testo o immagine fosse pubblicato in via inappropriata chiediamo agli Autori di segnalarci il fatto è provvederemo alla sua cancellazione dal sito